Security Assessment
Despite strong infrastructure hardening processes, devices often go unpatched or misconfigured due to the size of networks. Attackers often take advantage of vulnerabilities in routers, firewalls, DNS, web and database servers, and other systems to gain access to the internal network of an organization. Network Assessment is a critical tool that assesses, evaluates, and mitigates those risks.
Overview
- We identify and tests potential points of attack, after gathering background information by enumerating domains and identifying network blocks registered to the vendor. These attack vectors are first verified, then enumerated to look for available live hosts, ports, and services.
- The output of this testing is a network diagram with ports and services accessible from the Internet. Our team provides a list of vulnerable services along with the level of impact and recommended fixes, including those listed in the SANS/FBI Top 20 Most Critical Internet Security Vulnerabilities (www.sans.org/top20/). We also provide architectural recommendations for the DMZ.
- Discover vulnerabilities in a network
- Move beyond simple scanning with in-depth, non-intrusive assessments or, optionally, penetration testing
- External or internal assessments based on client requirements
Our Approach
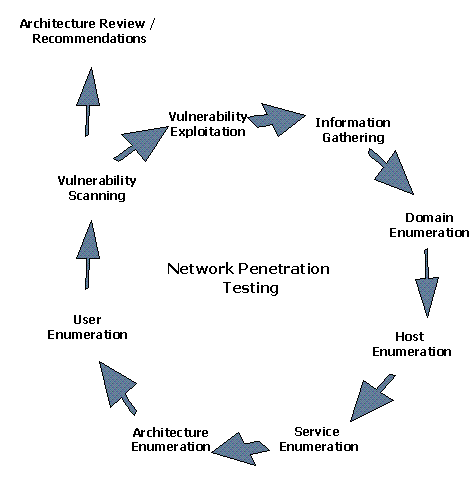
We emulate an attacker to gain access to the internal network. In order to do this, we iterate through the following steps for each layer of attack (e.g. web server, other Internet-facing hosts, DMZ, management network, internal network):
- Information Gathering—Gather background information about the company to create a corporate profile based on data found on the Internet
- Domain Enumeration / Network Block Enumeration—Create a detailed network map which helps the organization identify and overcome blind spots. Our consultants approach domain and network enumeration without significant prior knowledge about the company’s network.
- Host Enumeration—Identify available hosts through a variety of network scans, after verifying that the network blocks are owned by the company
- Service Identification and Enumeration—After enumerating the hosts, use Internet data to identify services (including version numbers) that are available on each host
- Architecture Enumeration—Develop an architecture diagram that details access controls, based on output from the previous steps. This helps clients understand what information a potential attacker can gather about the network from the Internet.
- User Enumeration—Identify user names and attempt brute-force authentication attacks on all Internet-facing web interfaces and devices. This phase is not performed unless explicitly requested by the company, to avoid locking out accounts.
- Vulnerability Scanning—Perform vulnerability scanning using the Nessus tool on the range of IP addresses that we identified on the Internet. No exploits are run at this time. This tool is only used to aid in the overall assessment; we will not simply provide or reiterate the raw results in our assessment.
- Architecture Review—Perform an architecture review using all the information gathered. This review requires interaction with the client’s networking group to provide the best results.
- Vulnerability Exploitation—Attempt to gain access to the network and determine the depth of access that an attacker can gain from the Internet. This step involves running exploits and is taken after coordinating with the client.
Deliverables
The result of a network assessment is a list of possible vulnerable systems (if any). Based on additional analysis (either by exploiting the server, running host review scripts or requesting information through the administrator), false positives will be removed. Additionally, recommendations to help improve the network architecture will be provided.
We will consolidate the deliverable from its physical security review analysis engagements along with the other components reviewed (war driving, war dialing etc). The report will summarize the project’s scope, approach, findings and recommendations.